Office 365 - Protecting user accounts with FIDO2 keys (TAP method)
FIDO2 based Passwordless technology allows users to use a USB key sign in to Azure AD (Microsoft Entra ID) without using passwords. Once enabled, the users will be able to sign in to their accounts and log onto their Windows 10 machines ( Azure AD (Microsoft Entra ID) or Hybrid AD joined) using FIDO2 Security keys. The access is still protected by two factors in this case: 1) having physical access to the security key and 2) PIN or Fingerprint (on devices with biometrics support) configured on the FIDO2 Security keys
FIDO2 keys as a security method is available with Microsoft Azure AD (Microsoft Entra ID) for already a couple of years now. Being the most secure access method available for Office 365 user access, enrolling FIDO2 security keys had a requirement of MFA to be configured for the users, which made it useless for use cases where users do not have (or do not want) to use multiple devices to log in. This has finally changed!
During the MS Ignite 2021 conference (which was held virtually this year as well), in addition to GA of Passwordless, Microsoft also announced a new feature, Temporary Access Pass in Azure AD (Microsoft Entra ID) (Preview), which will allow your end users to use only a FIDO2 Security key to access their account (this eliminates the requirement of having the MFA configured prior to that, which was the case before).
This guide will describe how the administrator can set Temporary Access Pass for a user, and how that user can subsequently enroll his/her FIDO2 security key:
Enable the Temporary Access Pass (TAP)
As this is a preview feature, it has to be enabled first. Global administrator and Authentication Method Policy administrator role holders can update the TAP authentication method policy. To configure the TAP authentication method policy:
- Sign in to the Azure portal as a Global admin and click Azure Active Directory > Security > Authentication methods > Temporary Access Pass.
- Click Yes to enable the policy, select which users have the policy applied, and any General settings

Note: make sure FIDO2 Security Key method is also enabled (it is on the same page). - You can keep the default TAP values for the time being. A full description of possible options is available here
Create Temporary Access Pass for a user
Now, lets create a temporary access pass for a user. The user should be allowed to use TAP (configured in the previous step). To add a TAP for a user, follow the steps below:Sign in to the portal as either a Global administrator, Privileged Authentication administrator, or Authentication administrator.
- Click Azure Active Directory, browse to Users, select a user, then choose Authentication methods.
- If needed, select the option to Try the new user authentication methods experience.

- Select the option to Add authentication methods.
- Below Choose method, click Temporary Access Pass (Preview).

- Define a custom activation time or duration and click Add

- Once added, the details of the TAP are shown. Make a note of the actual TAP value. You provide this value to the user. You can't view this value after you click Ok.

Adding a FIDO2 Key using TAP Login
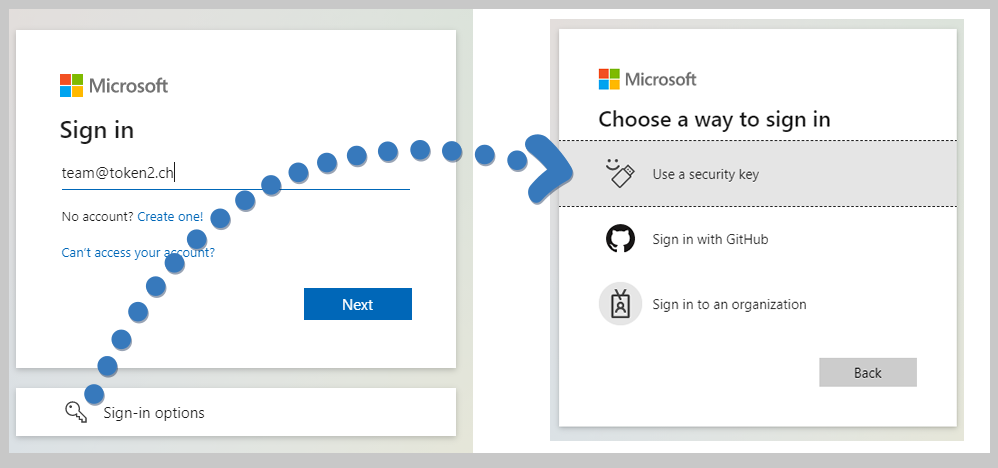
The steps below will allow a user to add a FIDO2 security key as the only authentication method for his/her account.- User needs to log out of all existing session or launch a web browser in Private (Incognito) mode
- Navigate to https://aka.ms/mysecurityinfo
- Enter the UPN of the account (the TAP was created for), such as user@token2.swiss
- If the TAP is valid, instead of the regular password and MFA prompt, the login form will ask for a temporary access pass

- After logging in with the TAP, the browser will redirect to the Security Methods page, where a FIDO2 key can be added
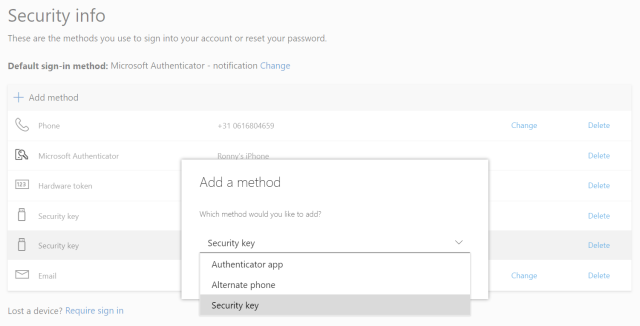
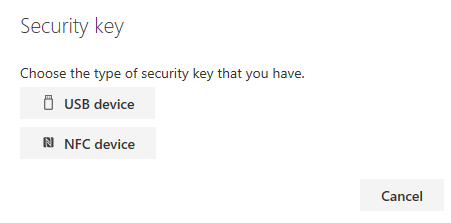
Add a FIDO2 Security key by clicking Add method and choosing Security key
Where to buy FIDO2 Security keys to use with this method?
 All of our FIDO2 keys are compatible with Azure AD (Microsoft Entra ID). You can place an order online or contact us for a quote. We ship worldwide* both with regular post and express services such as FedEx, UPS and DHL.
All of our FIDO2 keys are compatible with Azure AD (Microsoft Entra ID). You can place an order online or contact us for a quote. We ship worldwide* both with regular post and express services such as FedEx, UPS and DHL.
* - with the exception of Iran, India, Russia and a couple of other locations due to very complex customs clearance procedures
Video
Check out this video review demonstrating the process of the configuration of this method as well as user registration and login experienceFAQ
Question: Is a FIDO2 security key tied to just one Azure AD (Microsoft Entra ID)/Office 365 account?Answer: No, a FIDO2 security key isn't tied to a single Azure AD (Microsoft Entra ID)/Office 365 account. You don't need to purchase a separate key for every Azure tenant you access. Fortunately, you can use one key for multiple accounts! When logging in via Web interface, if multiple accounts (passkeys) for login.microsoft.com were created on the key, you will be asked to select the one to log in with. Please note that this applies to Web login method only, and not workstation login.
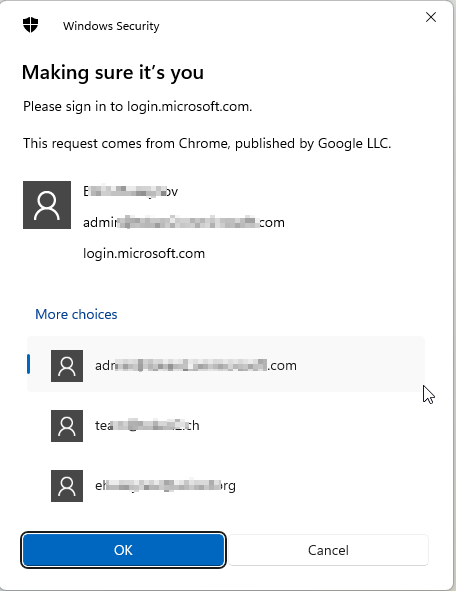
Question: Can I log in to Windows 10/11 Workstations using a key containing multiple Azure AD (Microsoft Entra ID) enrolled accounts?
Answer: Unfortunately, no. Signing in or unlocking a Windows 10/11 device with a security key containing multiple Microsoft Entra accounts is not supported. This scenario utilizes the last account added to the security key.
Question: As FIDO2 setup is self-service, how can I ensure my users do not select weak PIN codes, such as 1111 or 1234?
Answer: While the FIDO Alliance itself permits such PIN codes, the only restriction being the number of characters, this cannot be controlled by policies as the PIN is local to the security key. However, there is a solution available - Token2 PIN+Security Keys enforce PIN complexity at the firmware level, offering enhanced security measures.
- Automated Registration for Entra ID with PowerShell and GraphAPI
- Enrollment guide (standard)
- Enrollment guide (using Temporary Access Pass)
- Configure workstation passwordless login (Intune method)
- Configure workstation passwordless login (registry modification method)
- Configuring iPhone Mail apps for users only with Passwordless access
- Default MFA Method for Microsoft Entra ID
Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!

