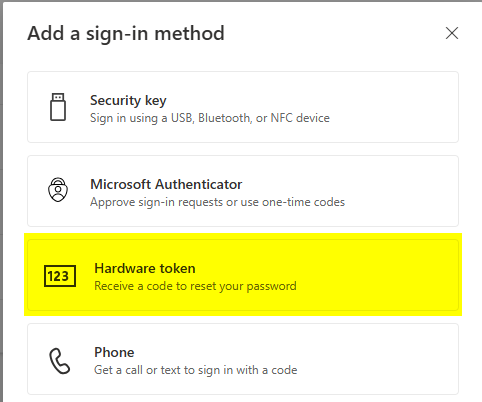
 A recent update to Microsoft Entra ID now allows end-users to self-service hardware OATH tokens, removing the need for administrators to manually activate them. Admins can upload hardware tokens into a "public repository" via Graph API, allowing users to assign tokens to their accounts independently.
A recent update to Microsoft Entra ID now allows end-users to self-service hardware OATH tokens, removing the need for administrators to manually activate them. Admins can upload hardware tokens into a "public repository" via Graph API, allowing users to assign tokens to their accounts independently.
Users simply enter the token's serial number and a 6-digit OTP from the hardware token to activate it. In addition, this improvement introduces support for SHA256 hashes for hardware tokens, enhancing security by providing a more secure hashing algorithm for token validation (which means our C203 can now be used with Entra ID). One more piece of good news is that there is no need to import the tokens using a global administrator account; a properly delegated Graph API permission is enough to perform the operation. Please note that a P1 or P2 premium license is still required for this feature.
Read our detailed guide on using this new feature here
Important!
While hardware OATH tokens provide a strong layer of security, TOTP is not 100% phishing-resistant. Unless other factors, such as USB being disallowed by policy, apply, we recommend using FIDO2 keys for a more phishing-resistant solution.
updates entra id azure ad
Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!
