Products
Buy options
4.34 GBPPlease check product and platform compatibility before placing an order
All pictures shown are for illustration purpose only. Actual product may slightly vary due to product enhancement or other reasons.
USB-A to Lightning adapter
Looking to use your FIDO2 USB-A key with your iPhone or iPad ? You'll need our FIDO2 USB-A to Lightning adapter to make it happen! This adapter is specifically designed to connect your FIDO2 USB-A key to your iPhone or iPad's Lightning port, enabling secure and convenient authentication for your iOS device. With its durable construction and easy-to-use design, our adapter ensures a seamless experience every time you need to authenticate with your FIDO2 key.
Additionally, there is another aspect that appears to be more of an iOS GUI glitch. When an iPhone prompts the user to choose the passkey type, users should start using the FIDO2 key without following the on-screen instructions.

We understand that security is a top priority for our customers, and we want to ensure that you have all the information you need to make an informed purchase. If you have any questions or concerns about our adapter or your FIDO2 key, please don't hesitate to contact us.
Blog
16-09-2025
Token2 PIN+ Keys Now Supported by MojeID at High Assurance Level
 MojeID, the Czech national digital identity service operated by CZ.NIC, has officially added Token2 PIN+ security keys to its list of devices accepted for the high assurance (úroveň záruky vysoká) level.
MojeID, the Czech national digital identity service operated by CZ.NIC, has officially added Token2 PIN+ security keys to its list of devices accepted for the high assurance (úroveň záruky vysoká) level.
18-07-2025
Windows 11 Update KB5062553 Breaks FIDO2 Security Key Management
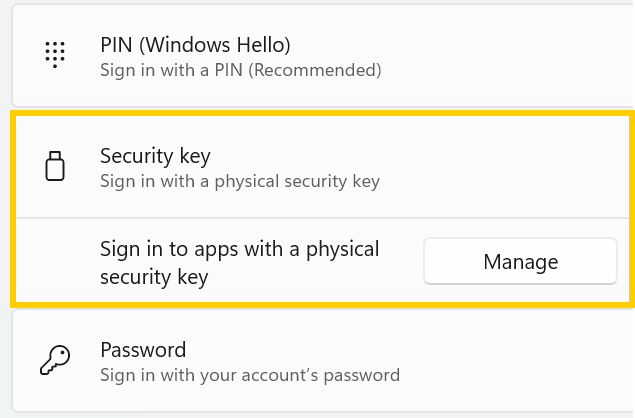 A recent Windows 11 update — KB5062553 — appears to have introduced a critical issue affecting FIDO2 security key management. Update as of 12 September 2025 – This issue is resolved in Windows 11 24H2 (build 26100.6584, KB5065426).
A recent Windows 11 update — KB5062553 — appears to have introduced a critical issue affecting FIDO2 security key management. Update as of 12 September 2025 – This issue is resolved in Windows 11 24H2 (build 26100.6584, KB5065426).
27-06-2025
Token2 PIN+ Bio3 Now Available
 Now Available: Token2 Bio3 – The First Biometric FIDO2 Key with Dual USB-A/USB-C Interface and iOS Fingerprint Management
Now Available: Token2 Bio3 – The First Biometric FIDO2 Key with Dual USB-A/USB-C Interface and iOS Fingerprint Management




















